What is a Tunnel in Networking?
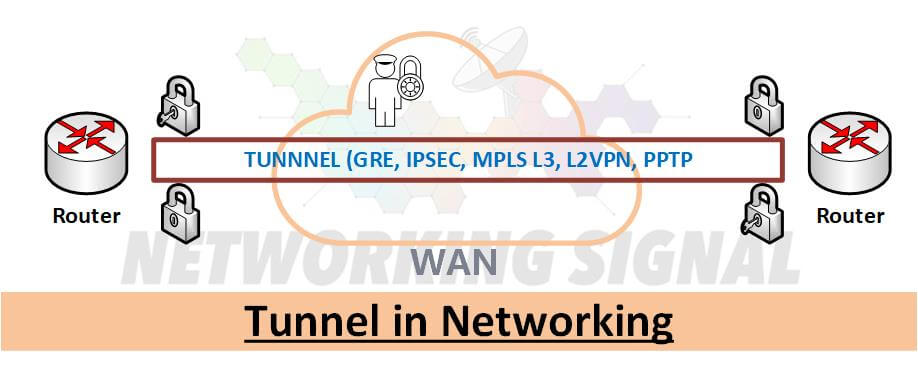
A tunnel is a connection between two computer networks, in which data is sent from one network to another through an encrypted link. This encrypted link ensures that the data passing through the tunnel cannot be read or intercepted by anyone who does not have the proper encryption key.
Tunnels are commonly used to secure data communications between two networks or to connect two networks that use different protocols.
- For example, a tunnel can be used to connect a company’s private network to the public Internet or to connect two separate private networks.
Tunnels can also be used to bypass firewalls and other security measures that may be in place on a network. By encapsulating data in an encrypted tunnel, it can be passed through a firewall without being detected or blocked.
Tunnels are typically created using software that runs on both ends of the connection. The software establishes the tunnel and handles the encryption and decryption of data passing through it.
There are a number of different protocols that can be used to create a tunnel. The most common protocols are PPTP, L2TP, and IPSec.
What are the Types of Tunnels in Networking?
1. Point-to-Point Tunneling Protocol (PPTP):
PPTP is a tunneling protocol that allows data to be passed through an encrypted link between two networks. PPTP is commonly used to connect a user’s PC to a remote server or to connect two remote servers.
2. Layer 2 Tunneling Protocol (L2TP):
L2TP is a tunneling protocol that allows data to be passed through an encrypted link between two networks. L2TP is commonly used to connect a user’s PC to a remote server or to connect two remote servers.
3. Internet Protocol Security (IPSec):
IPSec is a security protocol that can be used to create a secure tunnel between two networks. IPSec is commonly used to secure data communications between two networks or to connect two networks that use different protocols.
4. Secure Sockets Layer (SSL):
SSL is a security protocol that can be used to create a secure tunnel between two networks. SSL is commonly used to secure data communications between a web server and a web browser or to connect two networks that use different protocols.
5. Transport Layer Security (TLS):
TLS is a security protocol that can be used to create a secure tunnel between two networks. TLS is commonly used to secure data communications between a web server and a web browser or to connect two networks that use different protocols.
What are the benefits of using tunneling?
Tunneling can provide a number of benefits, including improved security and privacy, increased Efficiency, and better compatibility between different networks and devices.
1. Improved Security and Privacy: Tunneling can help to improve the security and privacy of data communications by encrypting the data that is passed through the tunnel. This means that anyone who tries to intercept the data will not be able to read it.
2. Increased Efficiency: Tunneling can also help to increase the efficiency of data communications by reducing the amount of data that needs to be sent. This is because only the data that needs to be sent is encapsulated in the tunnel, rather than the entire communication.
3. Better Compatibility: Tunneling can also help to improve the compatibility between different networks and devices. By using a tunnel, devices that use different protocols can communicate with each other.
What are the disadvantages of using tunneling?
There are a few disadvantages to using tunneling, including the potential for reduced security and privacy, and the need for additional hardware and software.
1. Reduced Security and Privacy: If data is not properly encrypted, it may be possible for someone to intercept and read the data that is being passed through the tunnel.
2. Need for Additional Hardware and Software: In order to create a tunnel, you will need to have special hardware and software. This can be expensive, and may not be available for all devices.
3. Limited Compatibility: Tunnels can only be used to connect two networks that use the same protocol. If you want to connect two networks that use different protocols, you will need to use a different type of tunneling.
4. Increased Latency: Tunnels can also increase the latency of data communications. This is because the data has to travel through the tunnel, which can take longer than if it was just sent directly from one network to the other.
What is the best tunneling protocol for needs?
The best tunneling protocol for your needs depends on a number of factors, including the type of data you are sending, the security and privacy you need, the compatibility of the devices you are using, and the latency you are willing to tolerate.
If you are just sending small amounts of data, such as email or instant messages, then any of the tunneling protocols will work. If you need a high level of security and privacy, then you should use IPSec or SSL.
If you need to connect two networks that use different protocols, then you should use TLS. If you are willing to tolerate a higher level of latency, then you can use any of the tunneling protocols.