What is Authentication?
Authentication is the process of verifying the identity of a user or device. Authentication can be used to control access to resources in a computer system, network, application, or within an organization.
The most common methods of authentication are username and password, biometrics such as fingerprint, retinal scan, or facial recognition, two-factor authentication (using a combination of something you know with something you have), and token-based authentication.
What are the Types of Authentication?
Single-factor authentication: Single-factor authentication is the most basic form of authentication and requires only one form of identification to gain access, such as a username and password.
Two-factor authentication: Two-factor authentication provides an extra layer of security by requiring two forms of identification. This could include something you know (username and password) and something you have (a physical key or a code sent to your phone).
Multi-factor authentication: Multi-factor authentication requires three or more forms of identification, typically including something you know (username and password), something you have (physical key or code), and something you are (biometric data such as a fingerprint scan).
What are the Benefits of Authentication?
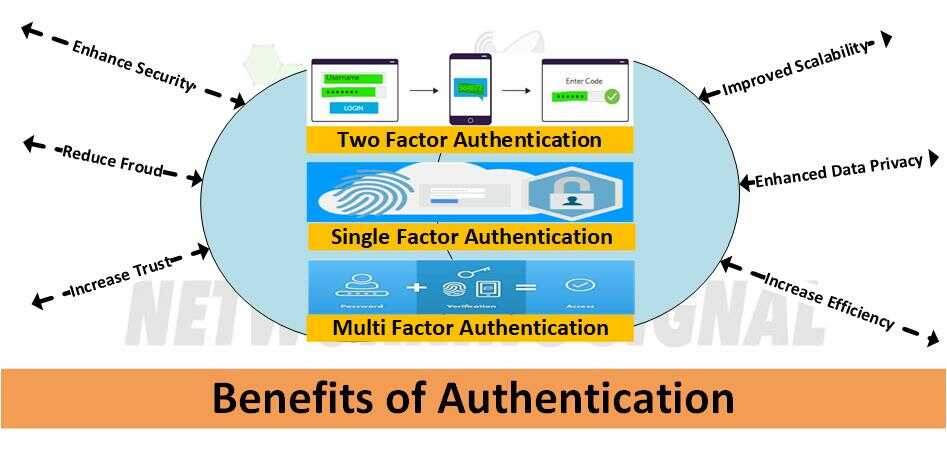
Here are just some of the benefits that come with using authentication:
- Enhanced security: Authentication provides an extra layer of security because hackers must now use multiple methods to gain access.
- Improved user experience: Authentication can help streamline the user experience by allowing users to quickly and securely access resources without having to remember multiple passwords or codes.
- Reduced fraud: With authentication, it is more difficult for hackers to impersonate legitimate users and commit fraudulent activities.
- Increased trust: Authentication builds trust with customers, partners, and other stakeholders by showing that your organization takes data security seriously.
- Enhanced compliance: Authentication can help organizations comply with regulations such as GDPR or HIPAA which require secure access to user data. It can also help organizations meet industry standards such as PCI DSS which requires authentication for credit card transactions.
- Improved scalability: Authentication systems are scalable and can be used to control access across an entire organization or a specific set of resources. This makes it easier to manage access on an ongoing basis and adapt quickly to changes in the organization.
- Enhanced data privacy: Authentication ensures that only authorized users have access to sensitive information, helping to safeguard user privacy and protect data from unauthorized use.
- Improved customer service: Automated authentication systems can help reduce customer wait times by quickly verifying user identity and providing access to the requested resources. This can result in improved customer satisfaction.
- Improved audibility: Authentication systems provide an extra layer of accountability, as they generate logs that can be used to track user activity and detect any unauthorized access attempts. This can help organizations identify security risks and address them quickly.
- Increased efficiency: Authentication systems allow users to securely access data and resources without having to remember complex passwords or PINs. This can help employees work more efficiently and quickly accomplish their tasks.
- Increased convenience: Authentication systems make it easier for users to access resources quickly and securely. This can result in improved user satisfaction and loyalty.
What are the Drawbacks of Authentication?
Despite the many benefits of authentication, there are also some potential drawbacks:
- Increased complexity: Authentication systems can be complex and difficult to manage. This can create a challenge for organizations that lack the resources or expertise to properly implement them.
- Potential cost: Authentication systems require investment in hardware, software, and personnel to ensure they are properly implemented and maintained.
- False positives: Authentication systems are sometimes prone to false positives, where legitimate users are mistakenly denied access. This can result in frustration for users and an increased workload for IT personnel.
- Privacy concerns: Some authentication methods, such as biometrics, may raise privacy or ethical concerns among users who are uncomfortable with their biometric data being collected and stored.
- Security risks: Authentication systems can be vulnerable to attacks such as brute force or phishing, which can compromise user data if not properly mitigated.
- Reduced usability: Some authentication methods may require users to remember multiple passwords or codes, which can reduce their overall experience with the system.
What are the Use Cases of Authentication?
Authentication can be used in a wide range of applications, from controlling access to physical spaces to protecting digital data. Here are some examples of authentication use cases:
- Device authentication: Authentication systems can be used to control access to computers, smartphones, and other devices. This helps protect the device from unauthorized use and keeps user data safe.
- Network authentication: Authentication can be used to control access to networks, including LANs, WANs, and the Internet. This helps ensure that only authorized users have access to sensitive data or resources.
- Application authentication: Authentication systems can control user access to applications such as email, web browsers, and other software programs. This helps protect the application from unauthorized use and keeps user data safe.
- Cloud authentication: Authentication systems can be used to control access to cloud-based applications and resources, such as storage and computing platforms. This helps protect the cloud environment from unauthorized use and keeps user data secure.
- Two-factor authentication: Two-factor authentication (2FA) requires users to enter two separate authentication factors, such as a password and a one-time code sent via text message. This provides an extra layer of security for user accounts.
- Biometric authentication: Biometrics are used to authenticate users based on their physical or behavioral characteristics, such as fingerprints or voice recognition. This helps protect user data from unauthorized access.
How Does Authentication Work in a Network?

The working of authentication in a network typically involves the following steps:
1. The user requests access to a resource or service.
2. The authentication system verifies the user’s credentials, such as their username and password.
3. If the credentials are valid, the authentication system grants access to the requested resource or service.
4. If the credentials are not valid, the authentication system denies access and may also log the attempt.
5. The user’s activity is monitored to ensure compliance with network security policies.
6. If necessary, additional methods of authentication such as two-factor or biometric authentication can be used to further secure access to the resource or service.
How We Can Authenticate Network Connections?
Here are the steps we can use to authenticate network connections:
1. Configure the authentication protocols and settings on both the client and server devices.
2. Establish a connection between the two systems using a secure communication protocol such as TLS or SSH.
3. Initiate an authentication process by sending the credentials from the client to the server.
4. Validate the credentials using an authentication protocol such as RADIUS or LDAP.
5. If the credentials are valid, grant access to the requested resource or service.
6. Monitor and log user activity for compliance with network security policies.
7. Disconnect the connection when it is no longer needed.
8. Implement additional authentication measures, such as two-factor or biometric authentication, if necessary to further secure the connection.
Authentication is important because it helps protect resources and data from unauthorized access. Authentication systems are used to verify the identity of users before they can gain access to sensitive information or resources. This helps ensure that only authorized users have access to confidential data, which reduces the risk of a data breach or other security incident.