What is Authentication Header?
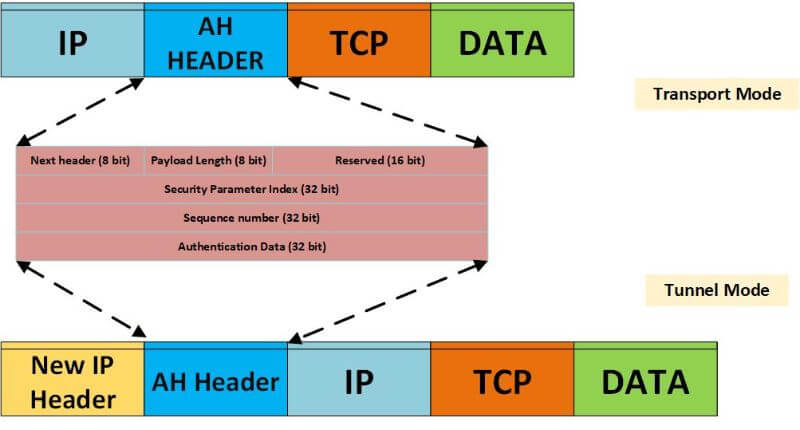
The Authentication Header (AH) is a member of the IPsec protocol suite. AH provides authentication and optional anti-replay service without providing confidentiality. Authentication is performed using a keyed message digest algorithm, in which a cryptographic key is used to create a digital signature over selected fields within the packet header.
Advantages of Authentication Header
AH offers a number of advantages over other methods of data authentication:
- AH can be used with all IP versions (IPv4 and IPv6).
- AH can provide protection against replay attacks.
- AH can authenticate all parts of the IP packet header, including fields that may be modified by network routers (such as the Time-To-Live field).
- AH can be used in conjunction with other security protocols, such as the Encapsulating Security Payload (ESP), to provide a complete security solution.
Disadvantages of Authentication Header
There are also some potential disadvantages associated with using AH:
- AH does not provide confidentiality for the data being transmitted. If data confidentiality is required, AH must be used in conjunction with another security protocol, such as ESP.
- AH can add overhead to the packet, which can impact performance. The added overhead is due to the necessity of including the message digest in each packet.
- AH may not be compatible with some older networking equipment that is not able to process the additional data in the packet header.
What is the www-authenticate header?
The www-authenticate header is an HTTP response header that is used to authenticate a user. The header contains a challenge that the user must respond to in order to gain access to the resource. The challenge typically consists of a username and password, but may also include other information, such as a security question or a one-time code.
How to decode the basic Authentication Header?
Here are the steps to decode the basic Authentication Header:
- Retrieve the value of the Authorization header.
- Remove the “Basic” keyword from the header value.
- Decode the base64-encoded string to obtain the username and password.
- The username and password are now separated by a colon (:).
Relationship Between NTLM Authentication and Authentication Header
NTLM authentication and the Authentication Header are two separate things. NTLM is a challenge/response protocol that can be used to authenticate a user. The Authentication Header is an HTTP response header that is used to authenticate a user.
The header contains a challenge that the user must respond to in order to gain access to the resource. The challenge typically consists of a username and password, but may also include other information, such as a security question or a one-time code.
The www-authenticate header is typically used in conjunction with the 401 Unauthorized status code.
NTLM authentication can be used in conjunction with the Authentication Header to provide a more complete security solution. However, NTLM authentication is not required in order for the Authentication Header to be used.
Relationship Between Authentication Header and Encapsulating Security Payload
The Authentication Header and the Encapsulating Security Payload are two members of the IPsec protocol suite. Both AH and ESP provide authentication for data being transmitted over an IP network.
However, there are some key differences between the two protocols:
- AH provides authentication for the entire IP packet, including the header fields that may be modified by network routers. ESP only provides authentication for the data payload.
- AH does not provide confidentiality for the data being transmitted. If data confidentiality is required, AH must be used in conjunction with another security protocol, such as ESP.
- AH can be used with all IP versions (IPv4 and IPv6). ESP can only be used with IPv6.

