What is ESP Encapsulating Security Payload?
ESP Encapsulating Security Payload is a data security protocol that provides confidentiality, authenticity, and integrity for data in transit. It is often used in conjunction with the Internet Protocol Security (IPsec) suite of protocols.
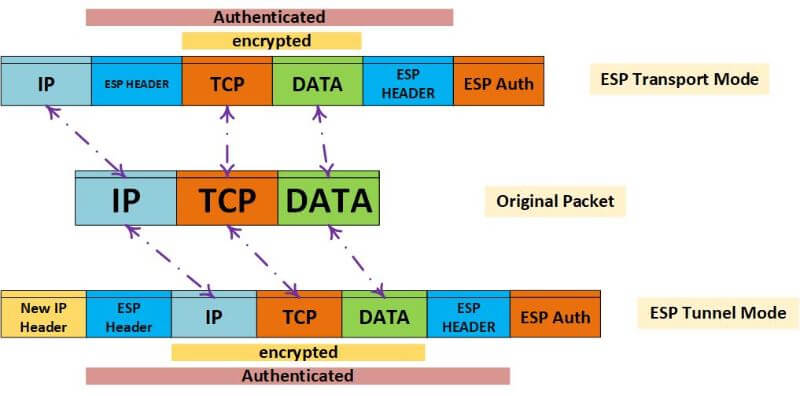
ESP uses a symmetric key algorithm to encrypt data and can optionally use an asymmetric key algorithm to authenticate the sender. ESP can be used in both transport and tunnel modes.
- In transport mode, ESP protects data at the IP layer.
- In tunnel mode, ESP protects data at the tunnel interface.
Parameter of ESA Encapsulating Security Payload
ESP has two main parameters:
- security parameters index (SPI)
- sequence number
The SPI is a 32-bit value used to identify a packet’s particular security association.
The sequence number is a 32-bit value used to protect against replay attacks.
ESP also has several optional parameters, such as the padding length, the IV, and the authentication data.
Advantages of ESP Encapsulating Security Payload
- ESP provides confidentiality, integrity, and authentication for data in transit.
- ESP can be used in conjunction with IPsec to provide a complete security solution for data in transit.
- ESP is transparent to applications and requires no changes to existing applications.
Disadvantages of ESP Encapsulating Security Payload
- ESP can add overhead to data packets, which can impact performance.
- ESP requires the use of a shared secret key, which must be exchanged between the communicating parties in a secure manner.
- ESP is a complex protocol and can be difficult to configure and troubleshoot.
How does encapsulating security payload work in IPsec?
Here are the steps of the process:
1. The sending host encapsulates the data to be protected with an ESP header.
2. The sending host encrypts the data using a symmetric key algorithm.
3. The sending host optionally authenticates the data using an asymmetric key algorithm.
4. The sending host sends the encapsulated and encrypted data to the receiving host.
5. The receiving host decapsulates the data and verifies the authenticity of the data.
6. The receiving host decrypts the data using a symmetric key algorithm.
7. The receiving host optionally authenticates the data using an asymmetric key algorithm.
8. The receiving host delivers the decrypted data to the application.
What is the Key size encapsulated security payload?
The key size for ESP Encapsulating Security Payload is 128 bits. We can use a larger key size, but it is not recommended as it can impact performance.
Importance of ESP in Cyber Security
ESP is a key protocol for providing data security in cyberspace. It is often used in conjunction with IPsec to provide a complete security solution for data in transit. ESP can help to protect data from eavesdropping, tampering, and replay attacks.

