What is Network Security Monitoring?
Network security monitoring (NSM) is the continuous process of identifying, detecting, analyzing, and responding to network attacks and threats. It is an important part of an organization’s overall security posture and helps ensure that networks are protected from malicious activity.
NSM generally falls into two categories:
- active
- passive
Active NSM involves using sensors and other devices to monitor network traffic for signs of malicious activity actively.
On the other hand, passive NSM relies on data already being collected by other systems, such as log files and intrusion detection systems (IDS).
See Also: Why Monitoring Your Application is Important?
Benefits of Network Security Monitoring
There are many benefits to implementing a network security monitoring program, including:
- early detection of attacks and threats
- improved incident response times
- a better understanding of attacker techniques
- identification of system and network vulnerabilities
- enhanced visibility into network traffic patterns
How to Monitor the Network Security?
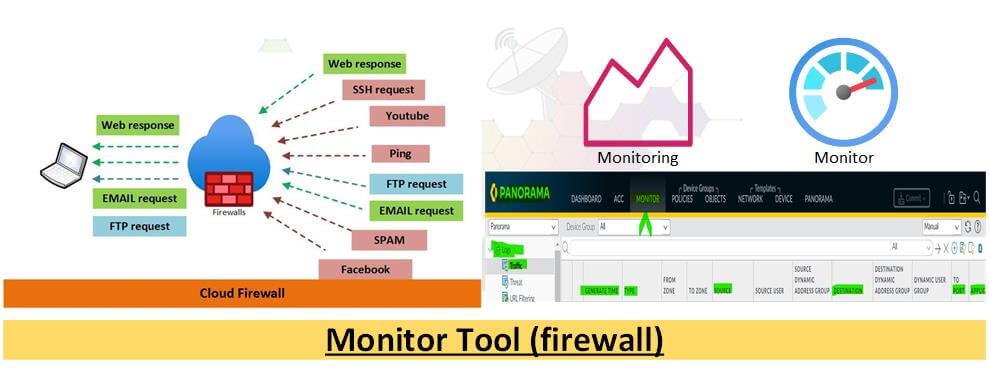
Use a Firewall
One of the best ways to monitor your network security is to use a firewall. A firewall is a piece of hardware or software that helps to protect your network from unauthorized access. Firewalls can be used to block incoming traffic from certain IP addresses or ports or to allow only outgoing traffic from certain IP addresses or ports.
Use Intrusion Detection and Prevention Systems
Another way to monitor your network security is to use intrusion detection and prevention systems (IDPs). IDPs are designed to detect and prevent attacks on your network. They work by monitoring network traffic and looking for patterns that may indicate an attack. If an attack is detected, the IDPS will take action to prevent it from happening.
Use Encryption
Encryption is another important tool that can help to monitor your network security. Encryption is a process of transforming readable data into an unreadable format. This makes it difficult for anyone who does not have the encryption key to access the data. When data is encrypted, it can only be decrypted by someone who has the encryption key.
Use Access Control Lists
An access control list (ACL) is a list of permissions that specify who can access what resources on a network. ACLs can be used to restrict access to certain IP addresses, ports, or protocols. They can also be used to allow only certain types of traffic from certain IP addresses or ports.
Monitor Network Traffic
Monitoring network traffic is another important way to monitor your network security. By monitoring traffic, you can see what type of traffic is flowing into and out of your network. This information can be used to identify possible attacks or vulnerabilities in your network.