What is Network Security Problems?
There are many potential network security problems that can arise from having an open and interconnected network. One of the most common security issues is data breaches, where confidential information is accessed without authorization. This can happen when hackers gain access to a network or when employees accidentally leave data exposed.
11 Network Security Problems
Here are some common network security problems that can occur:
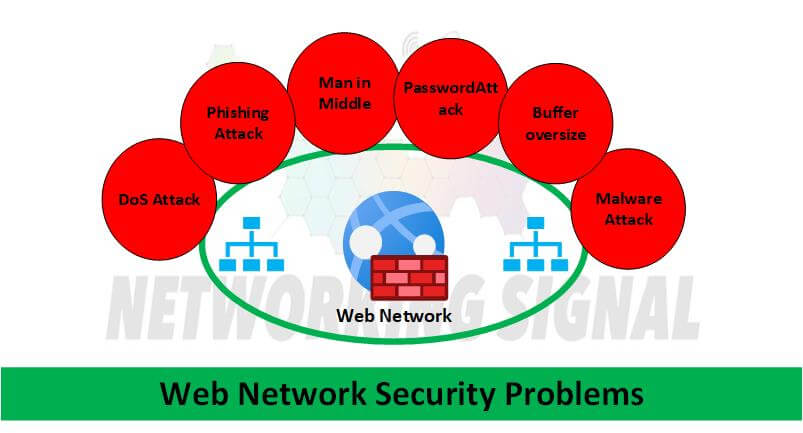
Denial of Service Attacks: A type of attack where hackers overload a network with requests, making it unavailable for legitimate users.
Man in the Middle Attacks: An attack where hackers intercept communications between two parties and can view or modify the data being exchanged.
Phishing Attacks: An attack where hackers send fraudulent emails or texts that appear to be from a legitimate source in order to trick users into revealing sensitive information, such as passwords or credit card numbers.
Password Attacks: An attack where hackers use brute force or dictionary attacks to guess passwords, or they may simply purchase lists of stolen passwords.
SQL Injection Attacks: An attack where hackers insert malicious code into a database in order to access sensitive information.
Cross-Site Scripting (XSS) Attacks: An attack where hackers inject malicious code into a website that is then executed by unsuspecting users who visit the site.
Distributed Denial of Service (DDoS) Attacks: A type of attack where hackers use a botnet, or a network of infected computers, to overload a target network with requests.
Malware Attacks: An attack where hackers install malicious software on a victim’s computer in order to gain access to sensitive data or take control of the system.
Zero-Day Attacks: An attack that exploits a previously unknown vulnerability in software or hardware.
Buffer Overflow Attacks: An attack where hackers send more data than can be stored in a memory buffer, resulting in the corruption of data.
Session Hijacking Attacks: An attack where hackers take over an active user session by stealing the victim’s session ID.
How to Protect Network Security?
There are many ways to protect network security, but some of the most effective include:
Using a firewall: A firewall is a hardware or software device that helps to filter traffic and prevent unauthorized access to a network.
- Cisco’s Firewall
- Palo Alto Networks
- Check Point
Implementing security policies: Security policies help to define what users are allowed to do on a network and what they are not allowed to do.
Using encryption: Encryption is a process of transforming readable data into an unreadable format that can only be decoded by authorized users.
- Sending an encrypted email
- Using a VPN to encrypt traffic
- Using SSL/TLS to encrypt communication
Keeping software up to date: Software updates often include security patches that help to fix vulnerabilities that could be exploited by hackers.
Training employees: Employees should be trained on how to spot potential security threats and what to do if they come across one.
Performing regular backups: Regular backups help to ensure that data can be recovered in the event of a security breach.
Some Web Security Problems
In addition to the general network security problems, there are also some specific web security issues that can arise. These include:
Cross-Site Request Forgery (CSRF) Attacks: An attack where a malicious website tricks a user’s browser into sending a request to another website without the user’s knowledge or consent.
Clickjacking Attacks: An attack where a malicious website tricks a user into clicking on a button or link that performs an unwanted action, such as installing malware.
Directory Traversal Attacks: An attack where hackers access files and directories that are outside of the intended directory structure.
Parameter Tampering Attacks: An attack where hackers modify the values of parameters in a URL in order to access unauthorized data.
Cookie Poisoning Attacks: An attack where hackers insert malicious code into a cookie in order to gain access to a victim’s account or track their online activity.