Port security is a feature of some network switches that limits the number of MAC addresses that can be learned on a particular port. This can help to prevent MAC address spoofing attacks, in which an attacker attempts to gain access to the network by impersonating another device.
Port security can be configured in a number of different ways, depending on the needs of the network. In its simplest form, port security can be configured to allow only a single MAC address to be learned on a particular port. This can be useful in situations where there is only one device that needs to be able to connect to that port.
How to configure port security on a Cisco switch?
There are a few different ways to configure port security on a Cisco switch.
A command for Maximum MAC Learn
The most basic way is to specify the maximum number of MAC addresses that can be learned on a particular port. This can be done with the following command:
switch(config)# mac-address-table static <max-mac-addresses> vlan <vlan-id>
This command will enable port security on the specified port and limit the number of MAC addresses that can be learned to the specified maximum. If more than the maximum number of MAC addresses attempt to connect to the port, then the switch will automatically shut down the port.
Example:
switch(config)# mac-address-table static 2 VLAN 10
In this example, we are configuring port security to allow a maximum of two MAC addresses to be learned on any port that is in VLAN 10. This can be useful if you have a small number of devices that need to be able to connect to that VLAN.
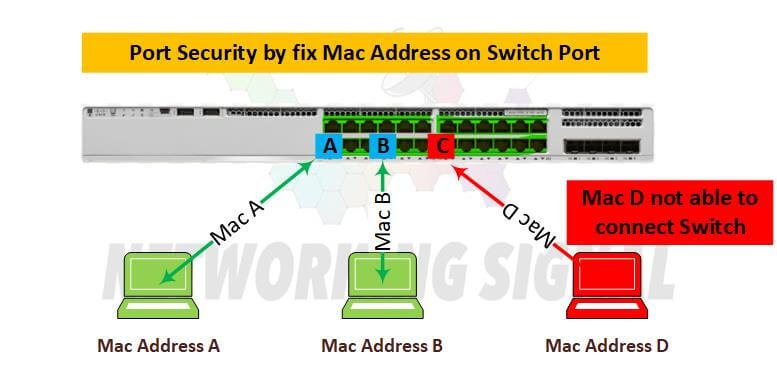
Command for Single MAC Learn
Another way to configure port security is to specify which MAC address is allowed to connect to the port. This can be done with the following command:
switch(config)# mac-address-table static <mac-address> VLAN <vlan-id>
Example:
switch(config)# mac-address-table static 00:11:22:33:44:55 vlan 10
This command will enable port security on the specified port and allow only the specified MAC address to connect to it. If any other MAC address attempts to connect, the port will be shut down.
By Using 802.1X
Cisco switches also support port security using 802.1X. This is a more sophisticated form of port security that allows devices to be authenticated before they are allowed to connect to the network. This can be useful in situations where it is important to ensure that only authorized devices are able to connect to the network.
To configure port security using 802.1X, the following command can be used:
switch(config)# aaa authentication port-access eap-based
This command will enable 802.1X port security on the switch. When a device attempts to connect to the port, the switch will send an EAP-Request message to the device. The device will then need to respond with an EAP-Response message that includes its credentials.
Types of Port Security
There are two main types of port security:
- Static
- Dynamic
Static port security is the simplest form of port security. With static port security, the MAC address of each device allowed to connect to the port must be configured manually. This can be done using the mac-address-table command, as described above.
Dynamic port security is a more sophisticated form of port security. With dynamic port security, the MAC address of each device allowed to connect to the port is learned automatically. This can be done using 802.1X or other methods.
Look Here:
Advantages of Port Security in a Network
Here are the advantages of port security:
- Ensures that only authorized devices are able to connect to the network
- Prevents malicious devices from spoofing the MAC address of a legitimate device in order to gain access to the network
- Prevents denial-of-service attacks that could be caused by a malicious device flooding the network with traffic from a spoofed MAC address
- Helps to conserve network bandwidth by preventing illegitimate devices from accessing the network
- Makes it easier to troubleshoot network problems because unauthorized devices are not able to access the network and cause issues
The drawback of Port Security in a Network
Here is the drawback of port security:
- It can be difficult to configure in a large network.
- Requires careful planning to ensure that all legitimate devices are able to access the network.
- If not configured properly, can cause legitimate devices to be denied access to the network.
- Can be bypassed by sophisticated attackers.
- It May not be supported by all devices.
Port Security: Switch vs Firewall
Now that we have seen how port security works, let’s compare it to firewalls.
- Port security is a type of network security that is implemented at the switch level. Firewalls, on the other hand, are implemented at the router level.
- Port security can be used to restrict which devices are allowed to connect to a network. Firewalls can also be used for this purpose.
- Port security is typically used to secure access to a LAN. Firewalls are typically used to secure access to a WAN.
- Port security can be bypassed by sophisticated attackers. Firewalls are much more difficult to bypass.
- Port security is not supported by all devices. Firewalls are much more common and are supported by most devices.
Overall, port security is a good way to secure a LAN. However, for a WAN, it is better to use a firewall.

