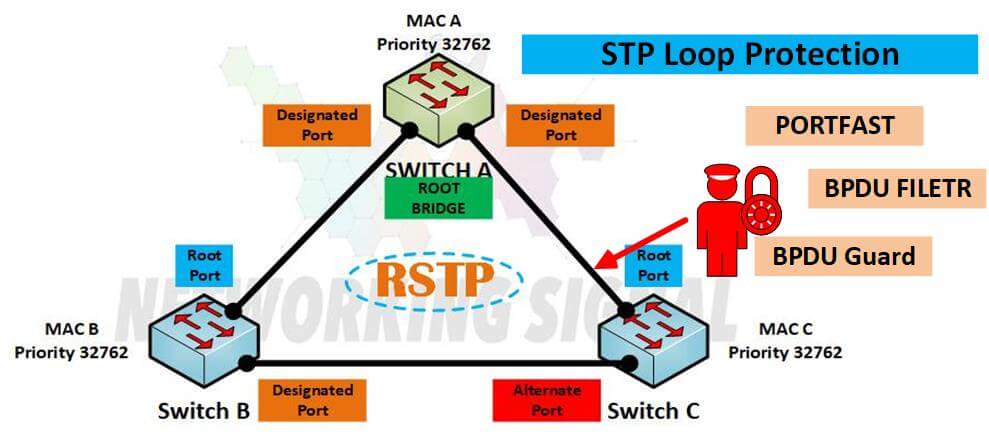
In this article, we learn how to work and use STP loop protection in the Cisco switch. We can use STP loop protection with CST, PVST+, and RPVST+. You can see here ( Networking Signal ) that this is a great way to prevent loops.
STP Loop Protection By Using Root Guard
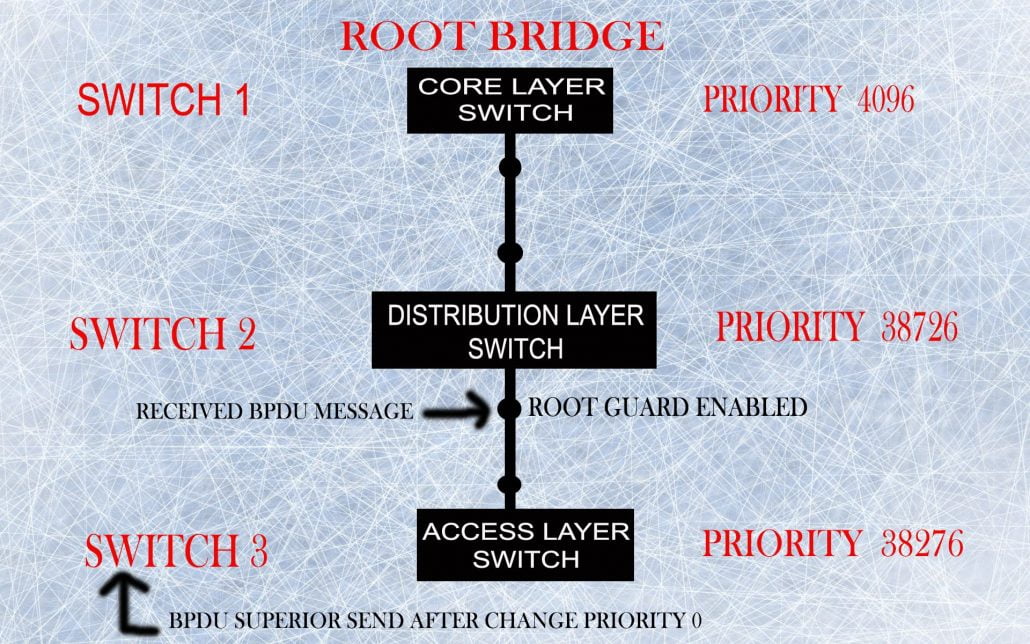
Root Guard: It is basically STP protection that deploys at distribution layer Switches. It is used to prevent access layer Switches from becoming ROOT BRIDGE.
For example three switches first core switch, 2nd distribution switch, and the 3rd access switch. Simply in network topology core layer switch always makes a ROOT BRIDGE. If by mistake ACCESS layer switch
If by mistake the ACCESS layer switch priority is less than the CORE switch (CORE switch priority 4096 and ACCESS switch priority 0) after this happens ACCESS layer switch sends a superior BPDU message to the Distribution layer Switch and on the DISTRIBUTION layer switch, no ROOT GUARD enables that’s why now ROOT BRIDGE change in the topology with ACCESS layer switch.
If ROOT GUARD is enabled on the DISTRIBUTION layer switch when superior BPDU is received on the DISTRIBUTION layer switch port then the same port goes to ROOT INCONSISTENCY STATE or BROKEN.
NOTE* In which VLAN port goes to inconsistency state only that VLAN traffic will be dropped on the same port. Other VLANs normally working.
STP Loop Protection By Using Loop Guard
LOOP GUARD: Loss of BPDU on the non-designated port then LOOP GUARD prevented it. We enable it on the root port and block the port. If loss comes then that port goes into LOOP INCONSISTENCY or BROKEN state.
When network topology any link behavior goes unidirectional then can be formed a loop. Does the first question come that how to create a unidirectional link?
An interface has two queues
1. Input Queue
2. Output Queue
It can be possible any queue congestion is high and that’s why BPDU is not processed. Then that link behavior goes unidirectional.
OSI model vs TCP/IP Model ( Comparison )
STP Loop Protection By Using UDLD
UDLD: Unidirectional Link Detection
It is a layer 2 protocol of CISCO. It works on FIBER PORT others work the same as LOOP GUARD. In fiber, there are two paths first send and the second receive, so that two echo messages send with an echo mechanism.
If only from one side echo message send or receive on this behalf UDLD declares to link is unidirectional and then the port goes to the ERROR_DISABLE state.
Bridge Assurance: It is a new technology. It is used in 6500 and 7000 Nexus series SWITCHES. In that type of switch, both switches send BPDU messages to each other to check the unidirectional link that technique is called BRIDGE ASSURANCE.
STP Loop Protection By Using BPDU Guard and Portfast
BPDU GUARD and PORTFAST: when we enable port fast on any port then the port changes our STP behavior like the below:
1. Port saves the STP converge time from 30 sec to 2 sec. (STP port converge time).
2. Port goes direct forwarding state. (not goes blocking> Listing>learning directly in Forwarding)
3. No TCN BPDU generate.
When PORTFAST enables the port received BPDU then switch the same port dissolve PORTFAST nature or loose and no PORTFAST work continues that problem is resolved by BPDU GUARD.
On the ACCESS layer switch, BPDU GUARD enables, when a BPDU message receives on the same port then the port goes to the ERROR-DISABLE state. But on the same port BPDU message forward continues. That problem can be
resolve by BPDU FILTER.
Configuration of globally PORTFAST enable: #SPANING-TREE PORTFAST DEFAULT By this command, PORTFAST enables on all access ports where BPDU msg not received. Configuration Globally of BPDU GUARD enable: #SPANING-TREE PORTFAST BPDUGUARD DEFAULT
By this command, BPDU GUARD enables on that port where port fast enabled.
BPDU FILTER: It is enabled on edge switches. Two types of BPDU FILTER we enable on Switch.
1. Globally
2. Per Port Basis
If we enable BPDU FILTER globally then the port sends 11 consecutive BPDU messages to check whether the neighbor device is an STP working device or not ( SWITCH or not). If the neighbor device is a SWITCH the STP is normally working. If a neighbor is not a switch then BPDU FILTER enables and functions.
If we enable it per port basis then we know that about port connection. PER PORT BASIS enables BPDU
FILTER not send or receive BPDU messages.
Configuration BPDU FILTER :
#SPANNING-TREE PORTFAST BPDU FILTER DEFAULT (Globally Enable)
Configuration-if
#SPANING-TREE BPDU FILTER ENABLE (Per port basis enable)
That all is about STP loop protection in CISCO SWITCH.

