What is SAML Authentication?
SAML authentication is an XML-based open standard used for exchanging information about authentication and authorization between parties, in particular, between an identity provider (IdP) and a service provider (SP). SAML is used to enable single sign-on (SSO), meaning that users only need to authenticate once to gain access to all of the applications that they are authorized to use.
Benefits of SAML Authentication
SAML authentication can provide a number of benefits over other authentication methods, such as:
Simplicity: SAML authentication is typically much simpler for users than other authentication methods, such as Basic or Digest authentication. Users only need to authenticate once to gain access to all of the applications that they are authorized to use. This can greatly reduce the number of passwords that users need to remember.
Improved security: SAML authentication can improve security by eliminating the need for users to send their credentials (such as usernames and passwords) to each individual service provider. This reduces the risk of these credentials being intercepted and used by unauthorized parties.
Increased flexibility: SAML authentication allows for a greater degree of flexibility than other authentication methods. For example, SAML authentication can be used to authenticate users to both local and remote applications.
How Does SAML Authentication Work?
SAML authentication typically works as follows:
The user attempts to access a service provider. The service provider redirects the user to the identity provider. The user authenticates with the identity provider. The identity provider issues an assertion to the user. The user presents the assertion to the service provider. The service provider verifies the assertion and grants the user access to the requested resource.
See Also: Global Protect VPN Not Connecting ( Issue Solved )
How to Integrate SAML Authentication in Azure Cloud to Global Protect?
Here are the high-level steps:
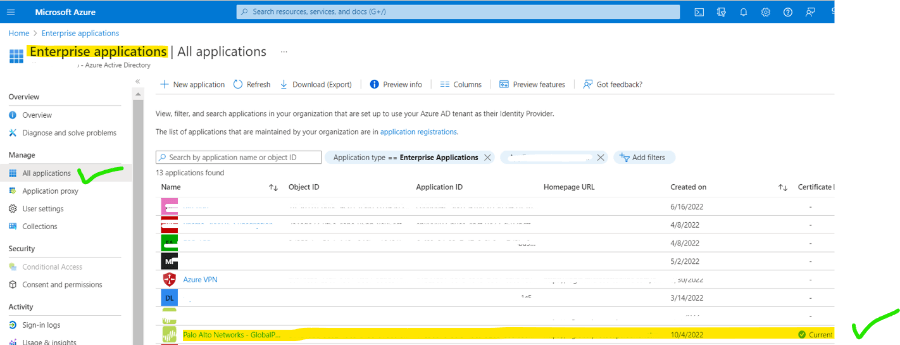
1. Open the Enterprise application and click on create. Search for global protection and create it.

2. Now the application has been created and open it for SAML configuration.
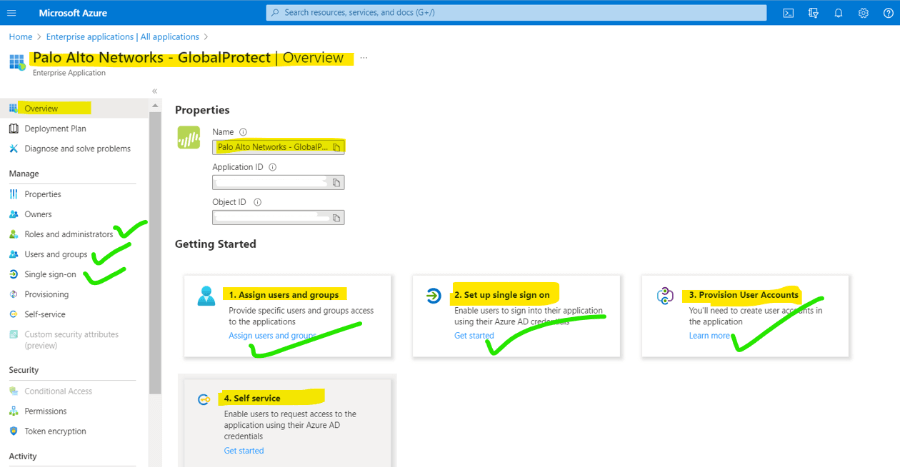
3. Click on assign user and add a user for the same which is on AD, then click on Single sign-on.
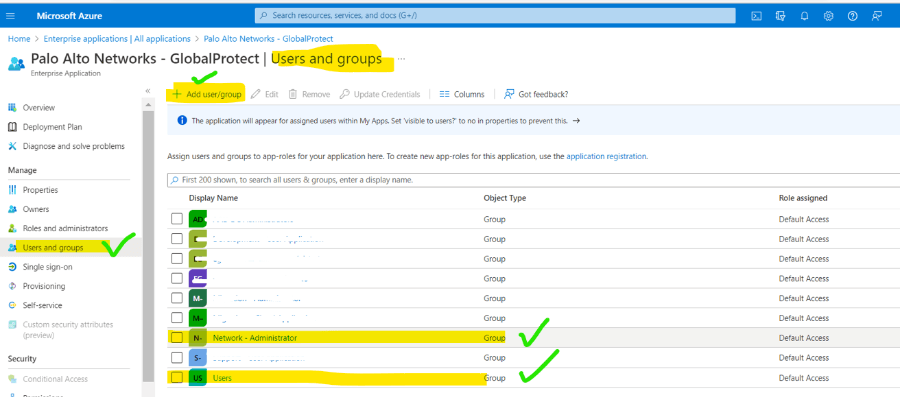
4. Goto users and groups and add needed users accordingly.
5. Goto SSO and add device URL as per SAML requirement and save it.
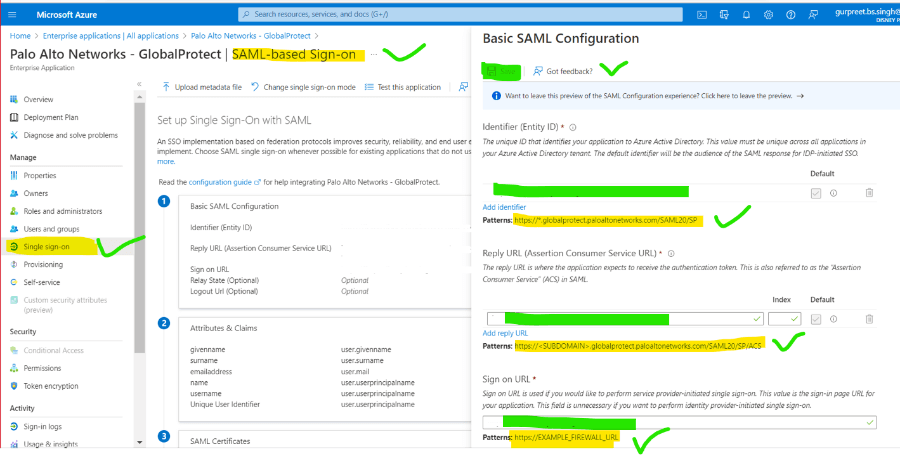
6. After Url saves download the XML file for integration to PaloAlto global protect.
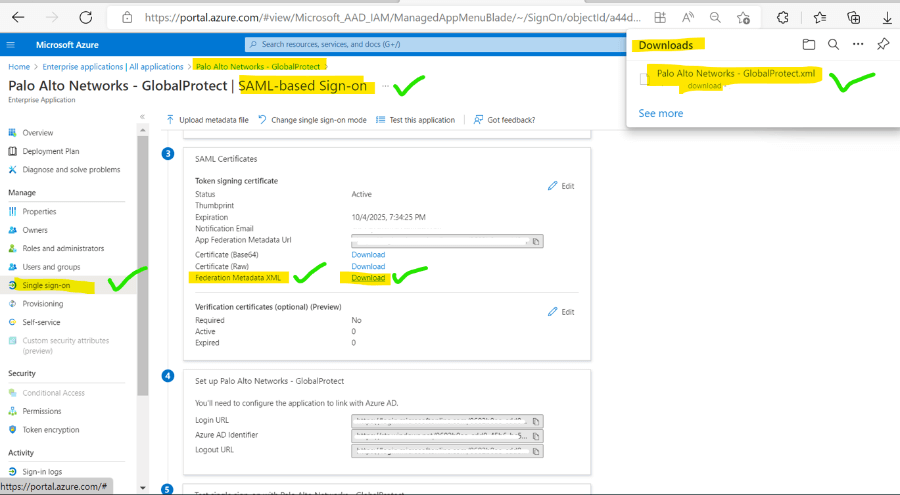
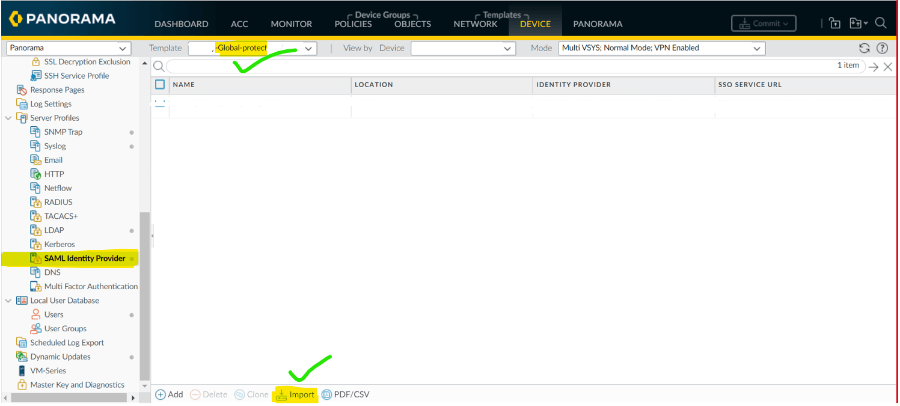
7 Open Panorama or Global Protect and go to SAML and import the XML certificate.
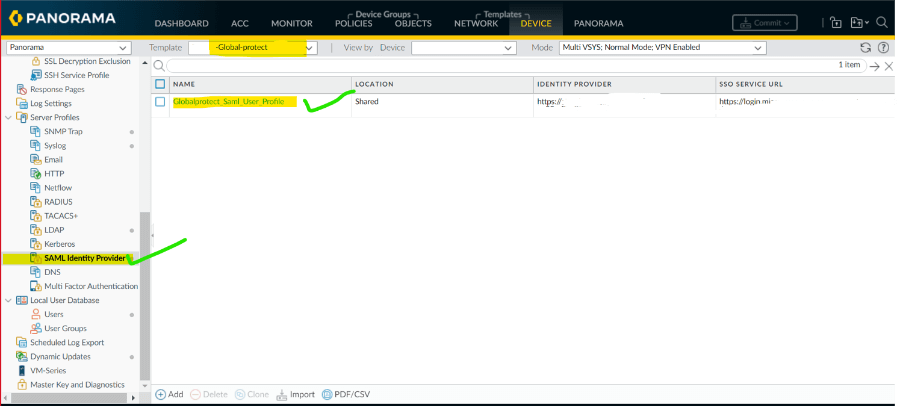
8. After uploading the XML user profile is created as shown.
9. Goto Authentication profile and add a new profile for SAML.
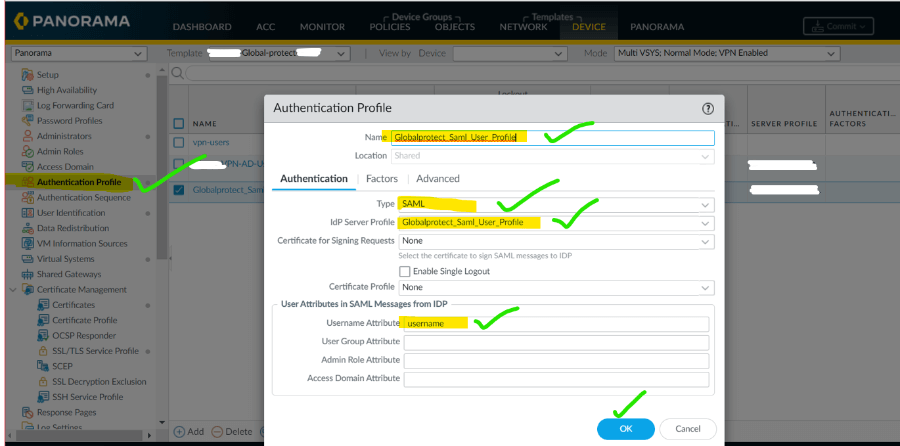
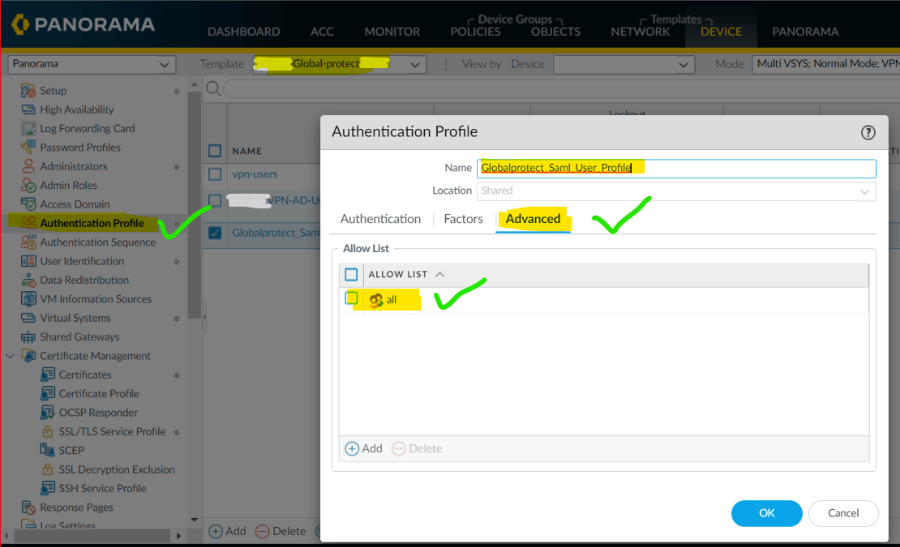
10. On the same profile go to advance and add users as per your enterprise requirement.
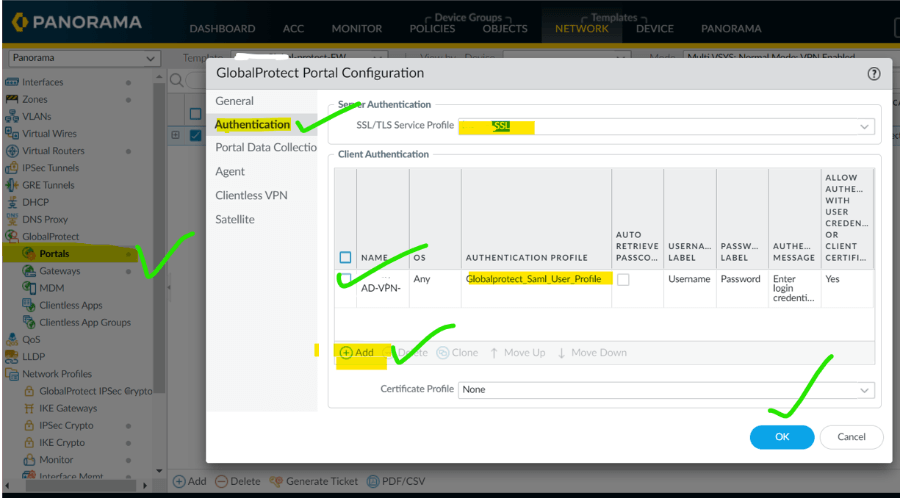
11. Goto portal and add SAML profile in the authentication.
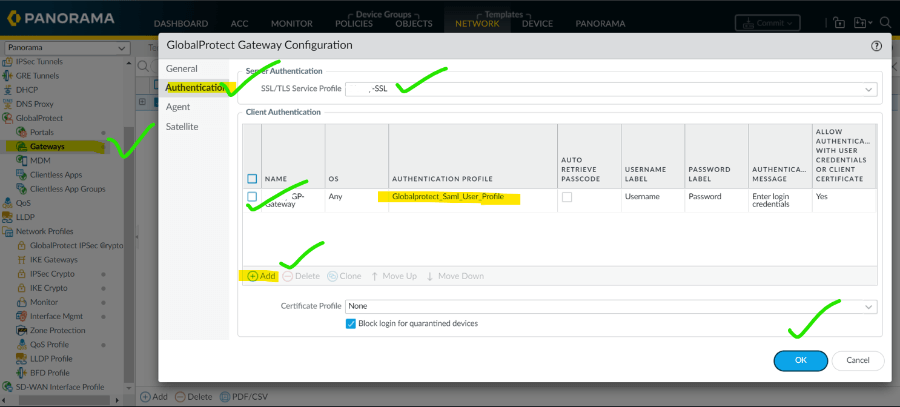
12. Goto gateway and add SAML profile in the authentication.
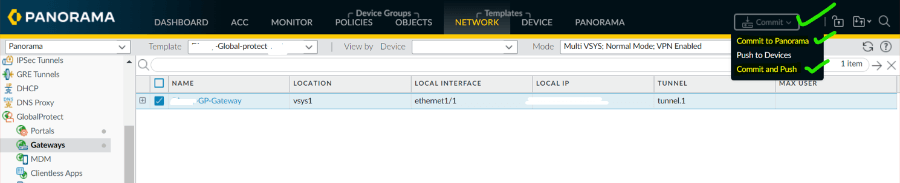
13. Now commit the changes, first on panorama and then push on the device according to your network need.