What is Encryption?
Encryption is the process of scrambling data so that it is unreadable to anyone who does not have the correct encryption key. This protects data from being accessed by unauthorized people and also keeps hackers and other malicious attackers from stealing or manipulating information. Encryption works by transforming plaintext (readable data) into ciphertext (unreadable data) using an encryption algorithm and an encryption key.
What are the Types of Encryption?
There are two main types of encryption:
- symmetric encryption
- asymmetric encryption
Symmetric encryption uses a single key to both encrypt and decrypt data, while asymmetric encryption uses two different keys (a public key and a private key).
Symmetric Encryption is the most commonly used type of encryption. It requires one key to both encrypt and decrypt data, which means that the same key must be shared between two parties. This can be a problem if one of the parties is not trusted, as it leaves the keys vulnerable to being compromised.
Asymmetric Encryption uses two different keys:
- a public key
- a private key
The public key is used to encrypt the data, while the private key is used to decrypt it. Asymmetric encryption is more secure than symmetric encryption because it does not require the same key to be shared between two parties.
There are also other types of encryption such as hash-based message authentication codes (HMACs), which use a cryptographic hash function to generate a unique message authentication code (MAC) which is used to authenticate the source of a message.
Encryption Key
An encryption key is a string of data used to control the process of encrypting and decrypting data. It is typically generated by an algorithm, which uses a combination of letters, numbers, and symbols. The longer the encryption key, the more secure it will be. Encryption keys are only effective if they are kept secret and never shared with an unauthorized third party.
Password-Based Encryption
Password-based encryption is a type of encryption that uses a password to protect data. It involves generating a key from the password, which is then used to encrypt and decrypt data.
This method is considered more secure than other types of encryption because passwords are generally harder for attackers to guess or compromise than encryption keys.
Password-based encryption also makes it easier to share encrypted data with other users, as they can simply use the same password to access the data.
Reset Encrypted Data
Reset encrypted data is data that has been encrypted, but then reset or re-encrypted to a different key or algorithm.
This is usually done when the original encryption key or algorithm needs to be changed for security reasons.
Reset encryption is especially useful for organizations that want to ensure their data remains secure and protected from unauthorized access. It also allows them to rotate encryption keys regularly, which further enhances security.
End-to-end encryption
End-to-end encryption (E2EE) is a type of encryption that ensures data is kept secure between two devices. This means that the data can only be accessed by the two communicating parties and cannot be decrypted by any other third party.
It also ensures that the sender and receiver are properly authenticated, so they know who they are communicating with. This type of encryption is often used to protect private messages sent over the internet, such as emails and instant messaging conversations.
Data Encryption Standard
The Data Encryption Standard (DES) is an encryption standard developed in the 1970s by IBM to protect data. It was adopted as a federal standard in 1977 and has since been replaced by more secure standards such as the Advanced Encryption Standard (AES). The DES uses a 56-bit key, which is not considered sufficiently secure for most applications.
Advanced Encryption Standard
The Advanced Encryption Standard (AES) is a symmetric encryption standard developed by the National Institute of Standards and Technology (NIST). It was adopted as a federal standard in 2002 and has since become one of the most widely used encryption algorithms.
The AES uses keys of 128, 192, and 256 bits in length, making it more secure than the Data Encryption Standard (DES). It is often used for data encryption on websites, as well as for encrypting files and other sensitive information.
Encrypted Email
An encrypted email is an email that has been encrypted using an encryption algorithm and key. Encrypted emails can be sent between two parties, ensuring that only the sender and receiver have access to the contents of the message. This helps protect private information from being viewed or manipulated by unauthorized third parties.
Encrypted DNS Traffic
Encrypted DNS traffic is a method of encrypting Domain Name System (DNS) queries and responses using Transport Layer Security (TLS). It helps protect user privacy by preventing third parties from intercepting DNS requests for private data. Encrypted DNS traffic can also help improve performance and reduce latency by reducing the amount of data that needs to be sent over the network.
What are the Advantages of Encryption?
Here are some of the advantages of using encryption:
- Protection of sensitive data: Encryption helps protect sensitive data from unauthorized access or theft. By encrypting the data, organizations can ensure that only those with the correct key can access it.
- Preventing eavesdropping: Encryption also prevents eavesdropping since any third party attempting to intercept the data will not be able to read it.
- Improved security: Encryption also improves overall security since it prevents hackers and other malicious actors from accessing or manipulating data.
- Data integrity: Encrypting data also helps ensure its integrity, as any changes to an encrypted file can easily be detected.
What are the Disadvantages of Encryption?
While encryption can offer many benefits, it also has some drawbacks.
- Key Management: One of the biggest challenges with encryption is key management, as the keys must be securely stored and properly managed in order to ensure their security.
- Computational Overhead: Encryption also requires a certain amount of computational overhead in order to encrypt and decrypt data, which can impact performance.
- Implementation: Implementing encryption correctly is also difficult, as it requires a deep understanding of cryptography and security protocols.
Additionally, many organizations are not aware of the best practices for implementing encryption and do not always use secure encryption algorithms or keys.
What are the Use Cases of Encryption?
Encryption can be used in a variety of contexts to protect data and ensure its security.
- Financial institutes: Financial institutions use encryption to protect customer data and prevent unauthorized access.
- Government organizations: Government organizations use encryption to protect sensitive information such as classified documents.
- Healthcare organizations: Healthcare organizations use encryption to protect patient records and sensitive information.
- Mobile apps: Mobile apps use encryption to secure data stored on devices and protect it from unauthorized access.
- Cloud storage providers: Cloud storage providers use encryption to protect data stored in the cloud and prevent unauthorized access.
- Internet of Things (IoT): IoT devices also use encryption to secure data communication between different devices.
- Home Networks: Home networks use encryption to protect data stored on the network and prevent unauthorized access.
- Office Networks: Office networks also use encryption to protect data stored on the network and prevent unauthorized access.
- Large Networks: Large networks such as internet service providers (ISPs) use encryption to protect data communication and ensure privacy.
- Email: Email services use encryption to secure communication between two parties and prevent eavesdropping.
- Website transactions: Website transactions use encryption to protect sensitive information such as credit card numbers and other personal information.
- Security Devices: Security devices such as firewalls and intrusion detection systems use encryption to protect data communication and ensure secure access.
- Online Banking: Online banking services use encryption to protect customer information and prevent unauthorized access.
- VoIP Services: VoIP (Voice over IP) services also use encryption to secure communication between two parties and prevent eavesdropping.
How Does Encryption Work in a Network?
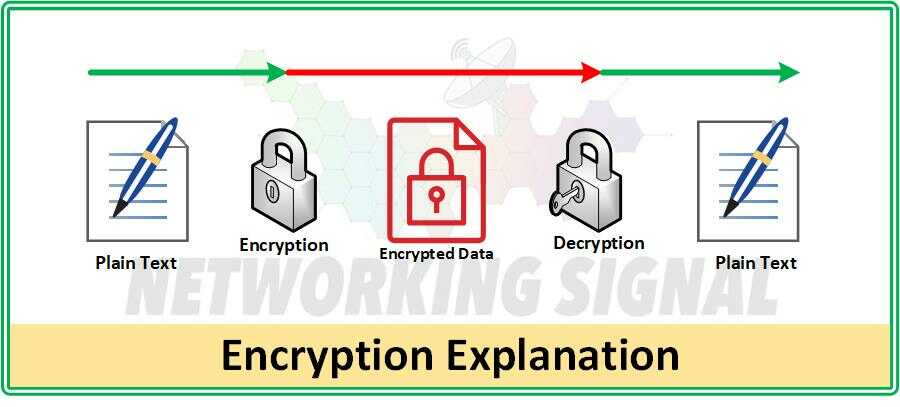
In a network, encryption is used to create an encrypted tunnel between two parties. This tunnel is then used for secure communication between the two parties. Data that is sent through this tunnel is encrypted and can only be decrypted with the correct keys. Encryption also prevents any third party from intercepting or manipulating data as it passes through the tunnel.
To ensure the security of an encrypted tunnel, both parties must exchange their encryption keys. This is done through a key exchange protocol such as Diffie-Hellman or RSA. Once the keys have been exchanged, data can be securely transmitted between the two parties without fear of interception or manipulation.
For example, let’s say two individuals want to securely communicate over the internet. In order for them to do this, they must establish an encrypted tunnel between their two computers.
- The first step is for both parties to exchange their public encryption keys using a key exchange protocol such as Diffie-Hellman or RSA.
- Once the keys have been exchanged, each party can encrypt the data they send using their own encryption key.
- The encrypted data is then sent over the internet and arrives at its destination where it is decrypted using the recipient’s private key.
- This ensures that only the intended recipient can decrypt and access the data.

